Defining Governance Strategy and finding just the right balance between administrative controls and freedom and flexibility is one of the most important pillars for successful Power BI implementation and long-term adoption. It is also one of the most challenging.
Configuring the Power BI tenant according to your identified governance and security needs also presents a unique challenge.
In this blog post we want to call out some easily overlooked ‘knobs and levers’ in Power BI Service that could potentially compromise enforcement of your organization-wide Power BI governance and security policies.
Unauthorized workspaces in Power BI Service
There are currently two types of workspaces in Power BI Service:
- Classic that are tied to Microsoft 365 Groups (they are controlled in Microsoft 365 Admin portal and are currently being phased out).
- New (also referred to as modern or V2) workspaces that are specific to Power BI Service and come with array of new features. These will be the focus of our conversation.
Many organizations choose – or are required by security and compliance rules -to restrict user’s ability to create new workspaces in the Power BI Service.
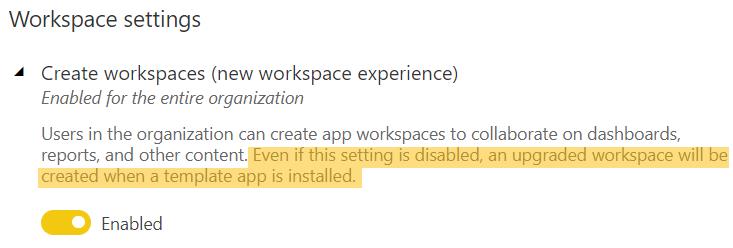
This ability is controlled in Power BI Admin portal by dedicated Power BI Service or Global admins via Create workspaces setting below:
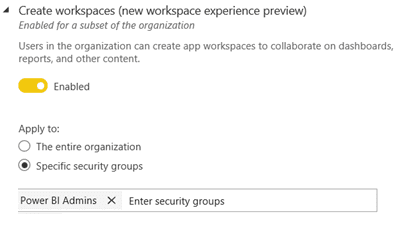
Limiting this to members of specific security groups can help avoid chaos and inconsistency within the tenant. Success here also relies on having the information readily available to all users on a) how they can request new workspaces to be created and b) on what they need to do to be added to the appropriate security groups.
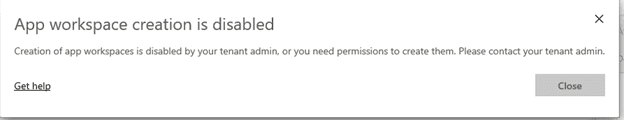
After enabling the change all users outside of the defined security groups will see this message if they try to create a new workspace and will be directed to contact the tenant admin.
Everything seems fine and clear as day and at this point most Power BI Service admins congratulate themselves on a job well-done and mark one task off their to-do-list.
Would we be writing this blog post if it were that easy? Of course, not.
Deep, deep down in the ever-expanding Tenant Settings list sits a frequently overlooked and seemingly innocuous setting controlling the user’s ability to Install template apps.
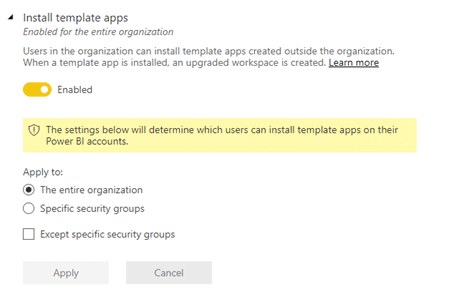
Those are the apps users often see in their ‘Recommended Apps section’ on the Home page in Power BI Service. There is also no way to our knowledge to turn these recommendations off or customize them in any way (e.g. limit to only internal content).
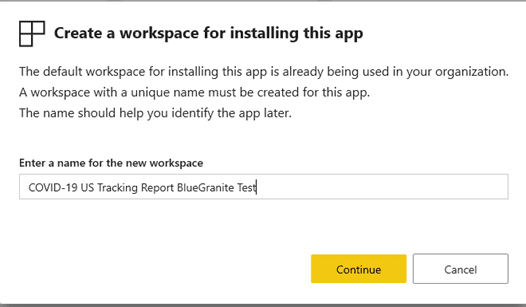
In the Install template apps setting menu we are presented with a notion, that a new upgraded workspace will be created to house the template app, but it is easy to overlook and, frankly, it took us here at BlueGranite quite a while to tie these two together.
So, what happens when the user with no workspace creation rights clicks on to install a template app?
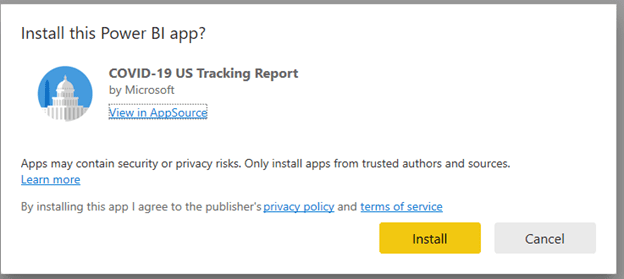
They are presented with an option to use default or create new V2 workspace to house this app:
After this initial install there is also nothing that prevents the user, who is now an admin of this shiny and new workspace to publish any other content to it.
In fact, they can also unpublish the app itself, remove all the template-app original content, rename the workspace, assign membership to other users and start using this new ‘illegal’ workspace as any other workspaces that has been created the ‘official’ way.
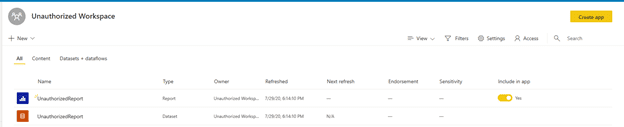
This could cause a serious governance and security loophole and, we think that this behavior should be addressed by the Power BI Team and we have reached out to notify them.
Update: As of 7/31 a new note has been added to the Settings pane to make the clarification:
However, as we are writing this, if you want to fully control which users are allowed to create workspaces within your Power BI tenant – make sure to use the same security groups for both Create workspaces and Install template apps settings.
There are quite a few other, more obvious inter-dependent tenant settings out there (e.g. Ability to reuse datasets across workspaces will not work if Export data is disabled as it controls Power BI Service live connection).
Wouldn’t it be nice if we had a clear dependencies list for all these settings notifying us which one overrides which, especially since new features and new tenant settings are introduced pretty often.
A Power BI Admin can dream… or vote for this idea.
Unauthorized Gateways in Power BI Service
Global and Power BI Service Administrators need to have full visibility into what gateways have been configured and are up and running on the tenant both in enterprise and personal modes. If I could get a cookie every time when, during discovery engagements, we ask the Power BI Admin team: “How many enterprise gateway clusters do you have up and running?” -and they confidently say : “This many” and it turns out to not be the case…I would have a lot of cookies.
If you are not using Power Platform Admin Center, you should!
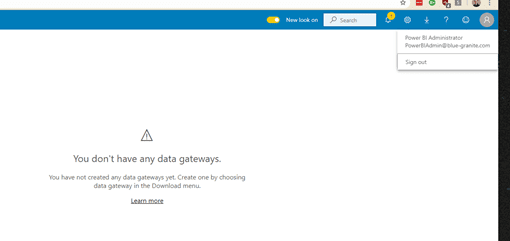
In Power BI Service even global administrators can only see the gateways for which they specifically have administration rights.
In example below we log in with a Power BI Administrator account and a friendly message notifies us that we do not have any data gateways:
To get to the full Tenant-wide view we could use PowerShell module or Power BI Rest API, or conveniently navigate to the Power Platform Admin Center. Since Data Gateways are used by all Power Platform tools along with Azure Logic Apps and Azure Analysis Services, it makes sense that overall administrative view would be in Power Platform Admin center, however it would also be nice to have a link to it in the same Power BI Admin portal UI.
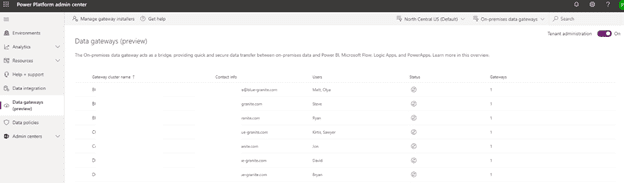
Logging in to Power Platform Admin Center with the same Power BI Administrator account we have a completely different picture:
Quick Tips:
- Make sure that ‘Tenant Administration’ toggle in the upper right corner is set to ‘On’ (it is only visible for global and Power BI service admins)

- Use the drop-downs to check:
- Whether there any data gateways configured in a different Geo location. By default, location is set to match that of the tenant, however it is possible to change during the installation process.
- Whether there are any gateways installed and running in personal mode.
As Power BI Service or global administrator, you can edit, rename, and remove any existing gateway, add new members, both in administrator and user roles and, most importantly, configure tenant-wide gateway installer policies to avoid future surprises.
The easy UI removal option comes in very handy. In many tenants there may be a lot of test or POC gateways, that have been set up once and uninstalled on the machine, but users failed to delete the gateways in the service.
I am ready to set the Tenant Gateway Policies now, how do I do this?
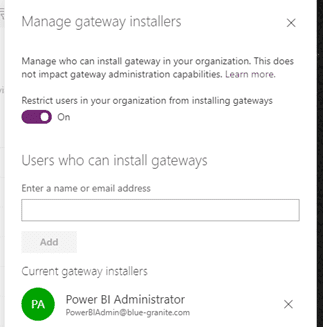
As we mentioned earlier, admins can use UI in Power Platform Admin Center to explicitly define users with Enterprise gateway installer rights.
Quick Tip:
- Currently groups are not supported so you will have to list individual users for this. All members of Data-Gateway-Admin group seem about right.
But what about data gateways running in personal mode?
Power BI Service interface makes it somewhat confusing for the end users and encourages them to install the personal gateway. We frequently see a proliferation of unmanaged personal gateways every time we come it to advise on existing Power BI Implementation, even though, it many cases, they were completely unnecessary.
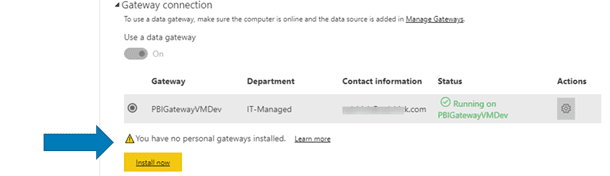
Depending on the gateway governance policies established for your Power BI implementation you may want to restrict that as well, or limit to a certain number or Power BI ‘power users’ running custom R and Python scripts, who have been through training and understand all the implications and limitations.
The only way to do it currently, is via specific commandlet in a DataGateway PowerShell module.
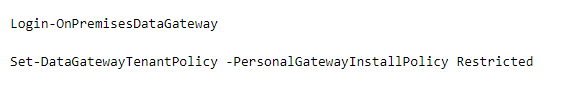
Quick Tips:
- This module requires PowerShell 7.0 and above for the full functionality.
- Changing the policy to Restricted will not remove or disable previously configured and running gateways in both modes for users that are not on the list. You would need to remove those either manually, in the Power Platform Admin Center, or by using PowerShell (after notifying the gateway owners and ensuring successful migration of existing solutions to official enterprise gateway, of course).
- Removal process will not uninstall the actual software; however, the users will not be able to sign in and will get ‘Unauthorized message’ if they try to install gateway on another machine.
Power BI Governance and Administration is a very involved process and, with so many frequent changes and additions, it is also something that should not be approached with a set and forget attitude.
We cannot recommend enough to invest time and effort in establishing an auditing and monitoring process as well as having recurring review and re-assessment of existing configurations to ensure that needs on both Business and IT sides are met.
If you are currently in the process of defining Power BI Governance and Security strategy and need help, please contact us to learn more about our Catalyst framework for Power BI Adoption.